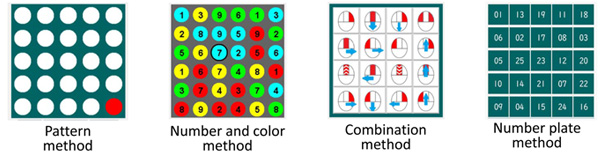
Research Subjects
Shoulder-Surfing Attack Resistant Authentication Methods
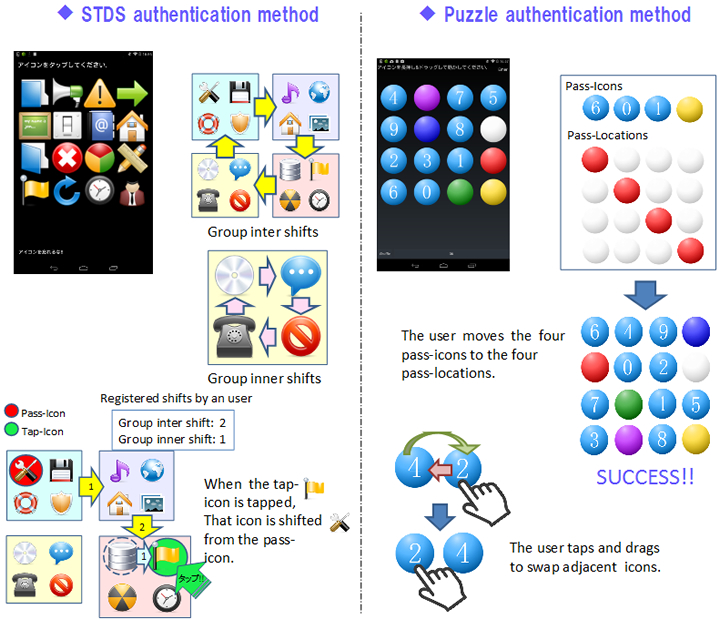
We proposed the following two shoulder-surfing attack resistance methods:
Rhythm Authentication Method
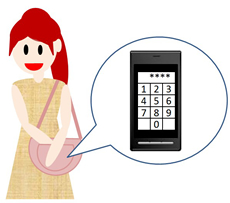
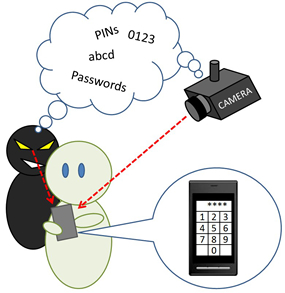
It is hard to prevent shoulder-surfing attacks, because we input numbers while looking at the screen.
Which makes us think...
"What if I could input numbers without looking at the screen?"

We proposed a rhythm authentication method in which a user taps the device screen using a pre-registered rhythm. The authentication information is the distances between and the strength of the taps.
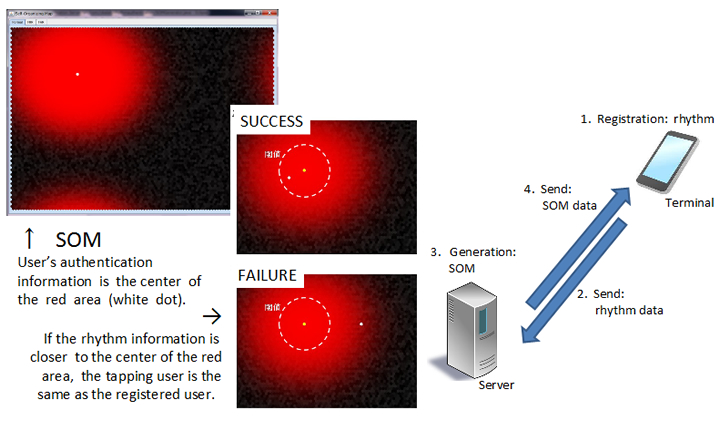
Registration of rhythm
- The user registers a rhythm into his or her terminal (hand-held device).
- The terminal sends rhythm data to the server.
- The server generates a self-organizing map (SOM) based on the rhythm data.
- The server sends the SOM data to the user’s terminal.
User authentication
- User input rhythm to user’s terminal.
- Terminal determines whether the user by comparing the rhythm data and SOM data.
Defending Against Cyber-Attacks
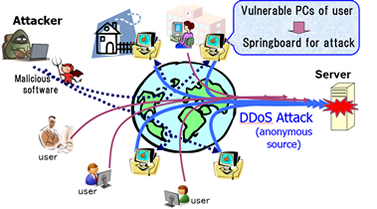
A cyber-attack is any type of offensive maneuver (such as a DDoS attack) employed by individuals or organizations against infrastructures, computer networks, and/or personal computers and handheld devices.
Assailants can attack targets using a variety of malicious actions, usually originating from anonymous sources, with the purpose of stealing from, altering, or destroying a specified target.
Most Internet service providers have established countermeasures to DDoS attacks in their network backbones. These devices can control available bandwidth while implemented proxy responses, but they often cut off valid communications because it is impossible to clearly discern legitimate users from hidden attackers.


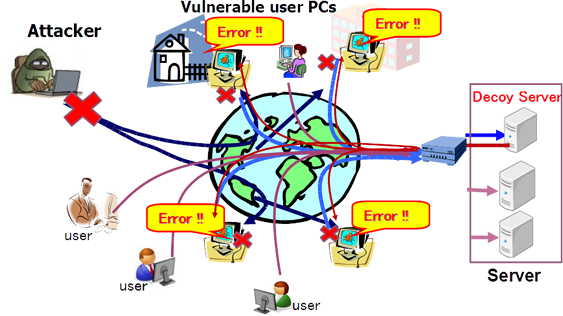
If legitimate users are hijacked or tricked
into attacking the server, the server displays
an error page informing them of the nature
of the attack and how to stop it.
When a server determines attacks are in progress, it records the interval between the session establishment and update times and then diverts any further incoming attack messages to the virtual Web server(decoy server).
If the attackers access the decoy server consecutively,
the actual server records the attacker’s IP address and
blocks communications from that source.
Security of Peer-to-Peer Network Systems
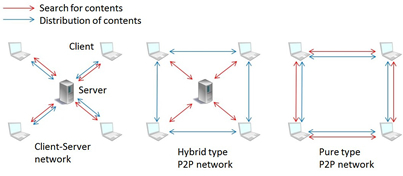
P2P systems are designed to allow sharing of computer resources (content, storage, CPU cycles) by direct exchange, rather than requiring the mediation or support of a centralized server.
P2P systems have internal dynamics that permit peers to join and leave the network at will. Every peer is connected virtually with other peers in the application layer of the network system structure so that all peers in the system compose a virtual network called an overlay.

Because administrators do not exist in P2P networks, it is hard to prevent illegal files from being uploaded. Information leakage arises from the transmission of viruses included in illegal files, so users must take positive steps to prevent viral infections.
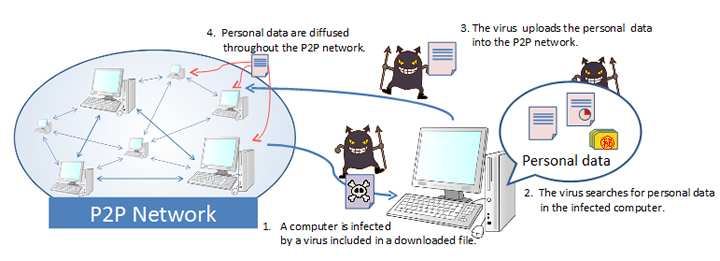

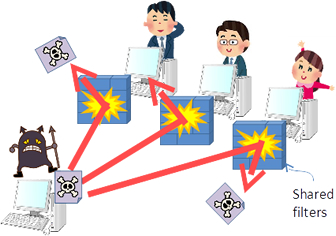
Since it is impossible to remove all illegal files from a P2P network, users who have weak filters are at particular risk from viruses diffused throughout the network.
We proposes an infection-prevention countermeasure built on shared filtering, in which all users share secure filters provided by users who have access to the best computer security.
Android Application Reviews User Evaluation System

Recently, leakage of the personal information from Android OS-powered devices caused by malicious applications is becoming a serious matter.
Android OS users must be careful not to install such applications.
It is very hard for most people to identify malicious applications on their own. Users must not only read information on how to use the applications, but also their permissions, and any available reviews from other users.
Oftentimes, users can find and read application reviews much easier than their related permissions. However, since most reviews are simple sentences that lack specific information, they are not helpful to new users.

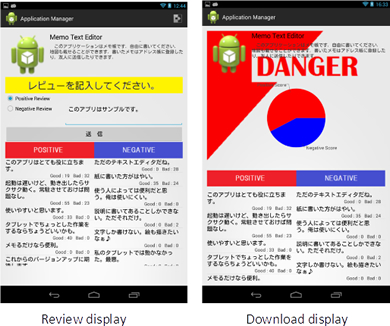
We proposed a review evaluation system that displays reviews from other users to new users who are contemplating whether the application would be useful enough to download. Then, based on his or her experience with the application, the new user can evaluate the earlier reviews as either positive (helpful) or negative (unhelpful).
These evaluation scores are sent to the people who wrote the reviews. This provides feedback that will help them to improve the quality of future reviews. Thus, useful reviews will become more noticeable.
Users can also confirm the usefulness of the application for him/her.
Secure Device Pairing Method
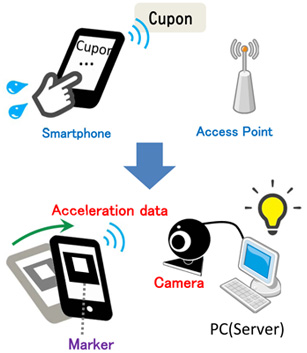

When entering the shop, coupon tickets are distributed only to terminals of special members. It is necessary to establish mutual authentication for safety wireless communication between the devices. This process is referred to "Secure Device Pairing". One approach to secure pairing is to use an additional physically authenticatable channel, which is governed by humans.

We propose the device pairing method which a camera recognizes the movement of a mobile device. The PC recognizes a marker on the display of the device and equates the movement of the marker with movement recorded by the device's accelerometer. It takes less time for the pairing because the user just moves the device.
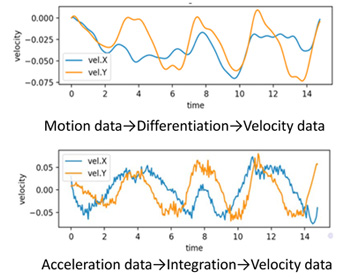

The device transmits the acceleration data to the PC wirelessly. The PC converts the motion data and acceleration data into velocity data. The server calculates the similarity between the velocity data. If the similarity is higher than the threshold value, the pairing is accepted.

The camera recognizes a marker, which is used in AR (Augmented Reality) technology, displayed on the device screen in order to detect the device movement.

We can consider various applications.

Mouse Authentication Methods
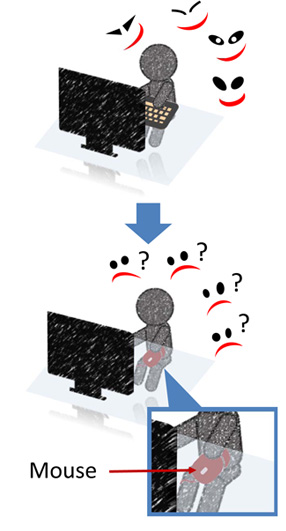

In the office and internet café, the password is stolen by peeking over the shoulder. This is called "Shoulder Surfing attack".

We proposed a mouse authentication method, which the user conducts authentication by mouse operations. The user can hide a mouse under the desk because the mouse is small. Therefore, this method is strong against shoulder surfing attack.

In this research, the authentication information is the multiple locations on a matrix. The locations is easy to remember than characters.
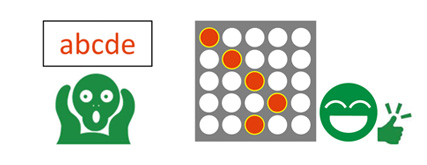
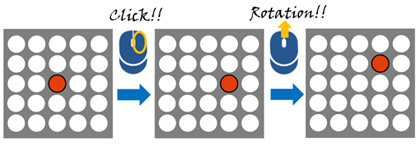

The operations in the method is simple.
ex1) move to the right by right click
ex2) move upwards by upper rotation

We have developed four variations.